The first question that I’m usually asked by clients is “Where do I even start?”. Good question! Here are a few points to consider:
- Do you patch ALL of the machines on your network diligently?
- Do you have a network firewall in place, and do you run antivirus on every client?
- Are your machines locked down (users are not using admin accounts, machines locked down, etc.)
- Is the software you use commercially supported (can you get patches for every piece of software and are you patching it (including that old legacy accounting system!))?
- Have your users been trained on internet safety and social engineering?
- Does your organization practice good physical security?
If you can answer YES to those three questions, you’ll probably defeat about 90% of the threats out there.
Here are a few facts for you:
- Most remote threats come from the exploitation of vulnerable software running on a user’s PC.
- Adobe products (Flash, Acrobat, & Shockwave), Microsoft Office & Windows, and Oracle Java make up probably 70% or more of the actively exploited vulnerabilities out there.
- COUNTERMEASURE: Keep these products patched, and you’ll avoid a lot of potential problems.
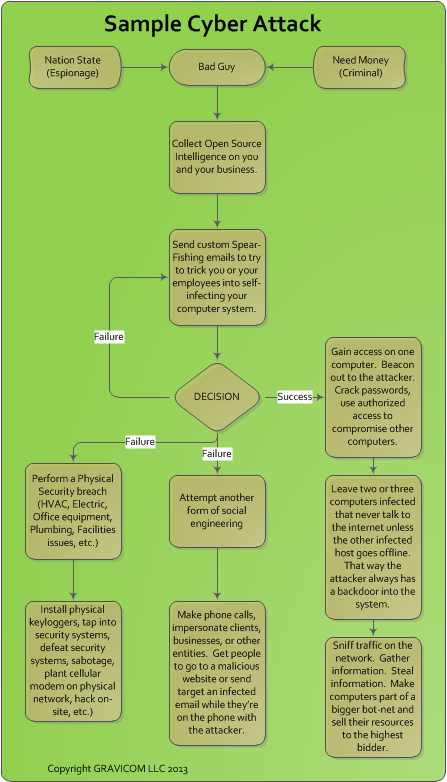
- Most hacks don’t come from the outside, most hacks come from people opening a spear-fishing email that infects their computer, which then beacons out to the attacker.
- Spear-Fishing emails are very convincing. A Spear-Fishing email is a custom-crafted email designed to trick a user into opening a link to an infected website or open an infected file.
- If your organization is truly the target of an attack the perpetrator will not relent until they get a successful compromise.
- COUNTERMEASURE: Train your users to spot suspicious emails and have a good enterprise filter in place.
- Many infections include key-loggers, which collect authorized logins that the attacker can use to penetrate your network.
- COUNTERMEASURE: Run Host Based Intrusion Detection Software / Intrusion Prevention Software (IDS/IPS)
- Once an attacker has a foothold on the target network, they use the infected machine to infect others. They infect several other machines inside the firewall so they always have a path back into the network in case the virus is discovered. This is called a “Digital Beachhead”, “Persistent Threat”, or “Advanced Persistent Threat”
- COUNTERMEASURE: Watch your logs! Look for suspicious behavior
- An attacker will run a cracking program on the infected computers to attempt to steal authorized usernames and passwords. They will most likely get the local administrator password, which many organizations use throughout the entire network. That allows the attacker to jump from machine to machine using fully authorized account credentials.
- COUNTERMEASURE: Set up auditing and check your logs regularly. Central log aggregation is a good thing.
- Many attackers will run sniffing programs from infected machines to see what kind of traffic is going to which computer. This helps them plan their attack.
- COUNTERMEASURE: Segment your network so that traffic can’t be intercepted.
- COUNTERMEASURE: Assure traffic is encrypted, even on the internal network.
- Many cyber attack campaigns go on for months and months. The average time from infection to discovery is 270 days (9 months).
I know the article above sounds like doom and gloom. In a sense it is, but remember the harder you make it for the attacker, the more likely it is that they will give up. They only have to be lucky once, you have to be lucky all the time.
To be lucky all the time, set up Defense In Depth measures, and understand what “normal” on your network and systems looks like. Have regular outside audits performed, do regular vulnerability scanning, patch constantly, and use good internet hygiene.
Fight the good fight!
Jamie Bass, CISSP-ISSEP
CEO, GRAVICOM LLC